Summary of the lab:
First part:
1. Configuration of ULA
2. Adding IPv6 static routes
3. Configuration of LLA
Second part:
1. Configuring of OSPF IPv4
2. Configuration of IPv6 subnets
3. Configuration of 6in4 tunnel
4. Adding IPv6 static routes
5. Testing and observing tunnel in Wireshark
Quick repetition of IPv6 addresses:
https://youtu.be/oItwDXraK1M?si=2ieEiBKZ_--bd7gY
IPv6 & IoT 2025: Lab: Playing with scoped addresses & 6in4 tunnel ©Tomas Palenik
This document is for lab exercises use only. Please do not copy or redistribute.
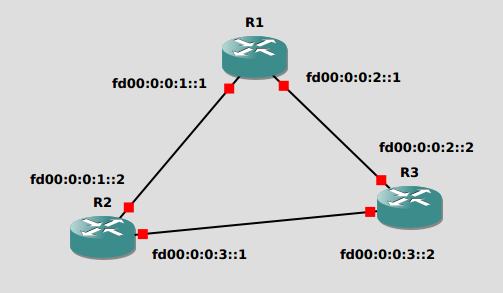
ULA and LLA
1. Configure ULA addresses:
2. Add proper static IPv6 routes to achieve full connectivity. Test connectivity.
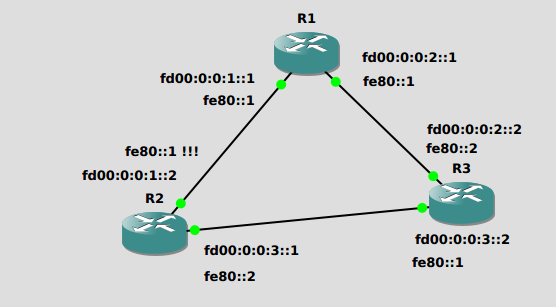
3. In the same topology, add link-local unicast addresses:
| a. | Use a slightly modified ipv6 address command:Router(config-if)#ipv6 address addr link-local |
b. Configure R1 router first.
c. In the figure, one address on R2 is intentionally set incorrectly. Try to set it anyway and
observe what happens.
d. Then replace the IID with ::2 and try again.
e. Try pinging the link local addresses.
IPv6 & IoT 2025: Lab: Playing with scoped addresses & 6in4 tunnel ©Tomas Palenik
This document is for lab exercises use only. Please do not copy or redistribute.
6in4: Tunneling IPv6 between branches over ISP with no IPv6 support
Configure dynamic routing for IPv4 using the OSPF protocol
1. Use the documentation provided in the previous lab.
2. Common IPv4 prefix: 20.25.0.0/16 – Subnet ID will be in 3rd octet.
3. Configure interface IDs according to Fig 1.
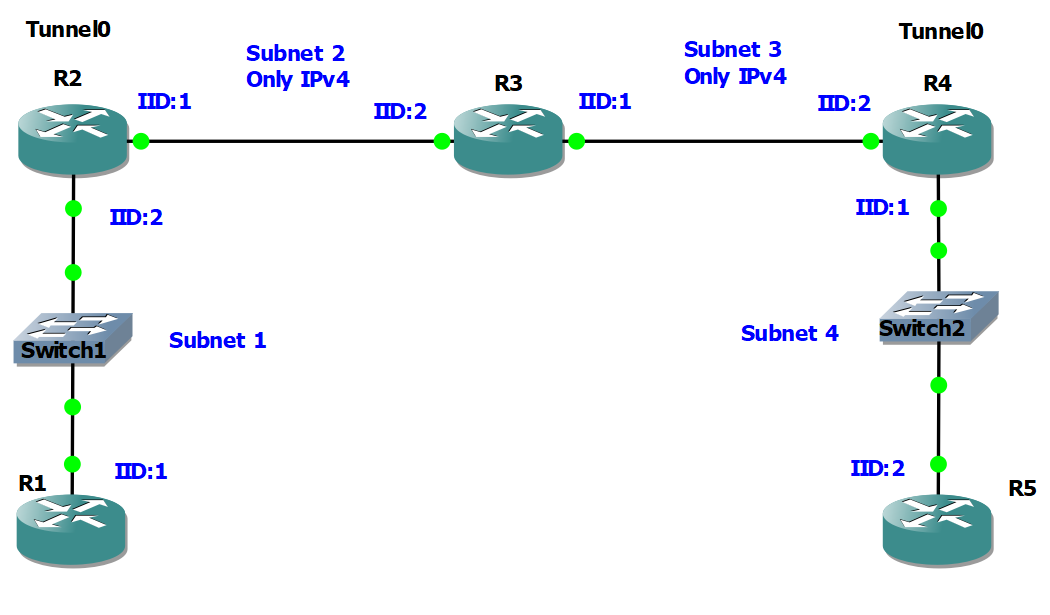
4. Configure OSPF protocol, user Router-Id: 1.1.1.1 for router R1, and similarly for other
routers.
Fig. 1: Topology with subnets and IIDs.
5. After successful IPv4 network convergence, try:
traceroute from R1 to R5
traceroute from R5 to R1
Observe the differences, and be ready to explain traceroute functionality.
6. Save configuration on all routers with command: Router#copy run start
IPv6 & IoT 2025: Lab: Playing with scoped addresses & 6in4 tunnel ©Tomas Palenik
This document is for lab exercises use only. Please do not copy or redistribute.
1. Configure IPv6 in Subnet 1 & Subnet 4 only
1. Common IPv6 prefix: 2001:abba:2025:0::/48 – Place subnet ID in 4th block.
2. Use the same Subnet ID and Interface ID as in IPv4 (as shown in Fig. 1).
3. Don’t forget to enable ipv6 unicast-routing on routers R1, R2, R4, R5.
4. On R4 change the LLA address of the interface within Subnet 4 to fe80::1 :
Router(config-if)#ipv6 address addr link-local
2. Connect IPv6 subnets by configuring a 6in4 tunnel from R2 to R4.
1. To configure a virtual tunnel interface use the following commands:
RX(config)#interface tunnel 0
RX(conf-if)#ipv6 address address/preflength Note: Use ULA addresses for tunnel endpoints:
fd00:dada::1/64 for R2 and fd00:dada::2/64 for R4
RX(conf-if)#tunnel mode ipv6ip
RX(conf-if)#tunnel source L2interfaceID (start node of the tunnel)
Note: L2interfaceID is interface ID of that represent start of the tunnel in IPv4 only subnet. ID or IP of interface can be used.
RX(conf-if)#tunnel destination IPv4address(far end node of the tunnel)
Note: destination IPv4address is IPv4 address of the interface at the end of the IPv4 subnet section
2. Test R2 and R4 “direct” connectivity (ULA addresses) using ping.
4. Configure static routing between IP6 subnets
1. Add just one IPv6 route on each of the routers R1, R2, R4, R5.
a. On R5 add static route to the remote network via the link local address on R4.
2. Do not add routes to fd00:: tunnel subnet from R1 and R5.
3. After route config you should see something similar:
a. On R1 the next hop address in for the static route should be global
b. On R5 the next hop address in for the static route should be LLA
4. Try Ping between Routers R1 and R5 using IPv6.
5. Try Traceroute between Routers R1 and R5 using IPv6 and IPv4.
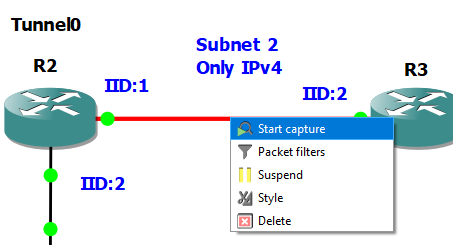
6. Open Wireshark at the link between R2 and R3. You can start packet capture by right clicking on
the link and selecting Start capture. Try ping and traceroute again. Observe encapsulation of
IPv6 inside IPv4 and traceroute operation.
IPv6 & IoT 2025: Lab: Playing with scoped addresses & 6in4 tunnel ©Tomas Palenik
This document is for lab exercises use only. Please do not copy or redistribute.
Playing with scoped addresses & 6in4 tunnel
Open Wireshark at the link between R2 and R3. You can start packet capture by right clicking on the link and selecting Start capture. Try ping and traceroute again. Observe encapsulation of IPv6 inside IPv4 and traceroute operation
